In my last blog post, I decided to create a survey as to get a better perspective on popular or favourite tools of attackers, red teamers and/or pentesters.
Below I present the results, with additional & minimal commentary from my side. Comments are below the figures. Note this is not fully indicative of an attacker or threat actor's arsenal, but I do hope it can give anyone some pointers. Enjoy the journey.
Yes, you may use this data as long as you mention the original source, which is this exact blog post. You may find a direct SurveyMonkey link to the results here.
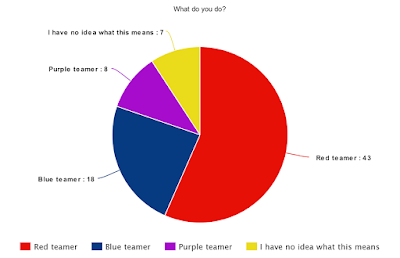 |
| Figure 1 - What do you do |
First and foremost question: what do you do? Are you a red/blue or purple teamer? Or no idea at all?
Most people that answered were red teamers. Awesome! If you have no idea what any of this means, or you are just starting with all this, then I definitely advise you to read the following:
The Difference Between Red, Blue, and Purple Teams.
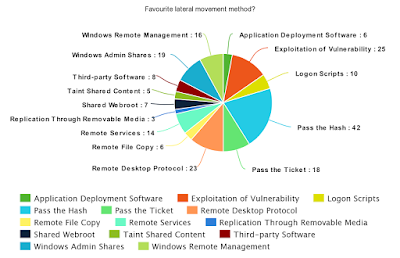 |
| Figure 2 - Favourite lateral movement method |
Answered: 66
Second question definitely yielded interesting results; with Pass the Hash (PtH) as most favourite or preferred method of lateral movement. Note that I shamelessly used this list from Mitre's excellent ATT&CK page on Lateral Movement here: https://attack.mitre.org/wiki/Lateral_Movement
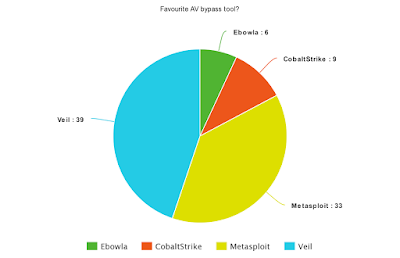 |
| Figure 3 - Favourite AV bypass tool |
Bypassing AV can be interpreted quite broadly, but let's say using the most well-known tools with ability to evaded AV - with which Metasploit takes the lead, and Veil a close second.
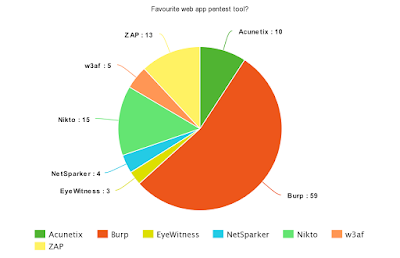 |
| Figure 4 - Favourite web app pentest tool |
Burp seems to have the biggest share of being most popular or used web app pentest tool.
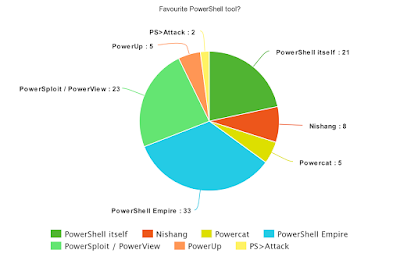 |
| Figure 5 - Favourite PowerShell tool |
This is definitely one of the, if not the most, interesting results of all questions. PowerShell Empire takes the lead, with PowerSploit following very closely... And not too far off is PowerShell itself. Draw your conclusions.
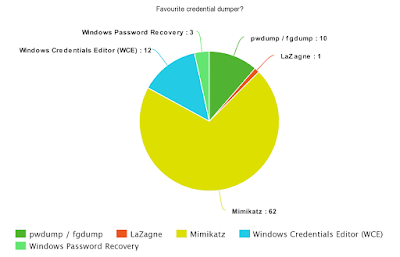 |
| Figure 6 - Favourite credential dumper |
Answered: 67
Mimikatz seems to be the most preferred credential dumper all around.
 |
| Figure 7 - Favourite password brute forcer |
Answered: 66
Hashcat, Hydra and John the ripper rank among the top three of password brute forcers.
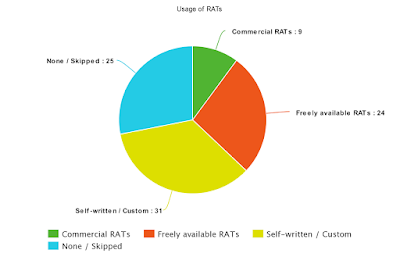 |
| Figure 8 - Usage of RATs |
Answered: 69
This question and the next overlap slightly - if an attacker doesn't (or can't) build custom malware, they may be more inclined to use RATs (freely available or not). Building a RAT is definitely more trivial than building or writing custom malware.
However, don't be fooled. If an attacker is strongly motivated, it's not a question of if they'll get on the network, but when. Take appropriate defensive measures.
Answered: 58
Repeating: attackers will not hesitate to use custom malware which is adapted or tailored to/for your environment! (and to evade any security controls or measures in place)
 |
| Figure 10 - Application Whitelisting bypasses |
Answered: 69
A rather surprising result, seeing 11 of the respondents either skipped, or didn't know what Application Whitelisting is. (and as such, how it may be bypassed)
I can definitely recommend you to check out Casey Smith's Catalog of Application Whitelisting Bypass Techniques.
Extra comments
... provided by some of the respondents yielded additional tools and information:
Lateral movement methods:
PowerUpSQL, CrackMapExecWin, smbexec, PowerSCCM, Kerberoasting, CobaltStrike (after obtaining admin creds for another system), WMI, Password reuse.
AV bypass:
PS Empire, PEspin, Shellter, Unicorn.py and even manually.
Web app pentesting:
metasploitHelper, Dirb, dirbuster, Kali2.
PowerShell tools:
Compress-File.ps1, BloodHound, PowerLurk, PowerSkype.ps1, PowerOPS, PowerForensics, Unicorn.py.
Credential dumping:
mimikittenz, go-mimikatz.
Password brute forcing:
Nmap NSE "brute"-category scripts, patator, Invoke-SMBAutoBrute.ps1, HashcatOCL.
RATs and malware:
Empire, Meterpreter (Metasploit), ADC2.ps1, ThinkPwn, manwhoami/Bella, tinymet/Ultimet, CobaltStrike beacons.
Conclusion
You may wonder if every attacker will use every tool on this list. They may well do so, or not use any of the tools and scripts discussed at all, and rather write everything tailored to your environment.
Also keep in mind that an attacker's TTPs may change over the course of weeks, months or even years. However, some tools will always be popular and withstand the test of time.
What's next?
I definitely advise you to either subscribe to feeds, or follow people on Twitter - both red teamers and blue teamers. Often, they both provide a unique insight which in turn will help you to defend better as well. Don't hesitate to share your findings with the community!
Try to think like an attacker. Leave nothing out. Know your own environment.
I'm not sure where to start.
What about PowerShell and all its misuses?
If your organisation has no need for it, disable PowerShell by configuring AppLocker. Note that PowerShell has many valid usages as well, such as logon scripts. There's a short blog post by Michael Schneider here that touches on this very subject: A story about blocking PowerShell
If you do want to use PowerShell, I advise you to upgrade to the latest version (currently v5) and turn on all the logging! A blog post worth reading: Greater Visibility Through PowerShell Logging
And the last one in regards to PowerShell is a very recent blog post written by Ashley McGlone:
Practical PowerShell Security: Enable Auditing and Logging with DSC
What about AV and how it can be bypassed?
AV should never be your only layer of protection. Next-gen or not.
What about... ?
Where there are attackers, there are defenders and vice versa. Use Event Logging. Use Sysmon.
I'm a red teamer, where can I find more information?
A recent post by Artem Kondratenk offers a ton of resources and insight:
A Red Teamer's guide to pivoting
Can I use this data?
Of course! As long as you mention the original source, which is this exact blog post. You may find a direct SurveyMonkey link to the results here.
Thanks to all the participants, and to you for reading!
Please do comment with your feedback or questions or anything else you would like to discuss.
I can definitely recommend you to check out Casey Smith's Catalog of Application Whitelisting Bypass Techniques.
Extra comments
... provided by some of the respondents yielded additional tools and information:
Lateral movement methods:
PowerUpSQL, CrackMapExecWin, smbexec, PowerSCCM, Kerberoasting, CobaltStrike (after obtaining admin creds for another system), WMI, Password reuse.
AV bypass:
PS Empire, PEspin, Shellter, Unicorn.py and even manually.
metasploitHelper, Dirb, dirbuster, Kali2.
PowerShell tools:
Compress-File.ps1, BloodHound, PowerLurk, PowerSkype.ps1, PowerOPS, PowerForensics, Unicorn.py.
mimikittenz, go-mimikatz.
Nmap NSE "brute"-category scripts, patator, Invoke-SMBAutoBrute.ps1, HashcatOCL.
RATs and malware:
Empire, Meterpreter (Metasploit), ADC2.ps1, ThinkPwn, manwhoami/Bella, tinymet/Ultimet, CobaltStrike beacons.
Conclusion
You may wonder if every attacker will use every tool on this list. They may well do so, or not use any of the tools and scripts discussed at all, and rather write everything tailored to your environment.
Also keep in mind that an attacker's TTPs may change over the course of weeks, months or even years. However, some tools will always be popular and withstand the test of time.
What's next?
I definitely advise you to either subscribe to feeds, or follow people on Twitter - both red teamers and blue teamers. Often, they both provide a unique insight which in turn will help you to defend better as well. Don't hesitate to share your findings with the community!
Try to think like an attacker. Leave nothing out. Know your own environment.
I'm not sure where to start.
Why not start by checking out a real live intrusion that happened, featuring APT29? There's an excellent presentation out there by Matthew Dunwoody and Nick Carr here:
Another excellent blog to check out is: http://adsecurity.org/
I additionally advise you to check out Matt Swan's Incident Response Hierarchy of Needs. If you like hierarchies or pyramids. definitely check out the threat intelligence Pyramid of Pain by David Bianco.
There's also a good paper on detecting lateral movement in Windows infrastructure by CERT-EU.
Lastly, check out JPCert's excellent report on lateral movement here:
Still in doubt? Start Googling some of the TTPs mentioned above and check out their functionality - and shortcomings!
If your organisation has no need for it, disable PowerShell by configuring AppLocker. Note that PowerShell has many valid usages as well, such as logon scripts. There's a short blog post by Michael Schneider here that touches on this very subject: A story about blocking PowerShell
If you do want to use PowerShell, I advise you to upgrade to the latest version (currently v5) and turn on all the logging! A blog post worth reading: Greater Visibility Through PowerShell Logging
And the last one in regards to PowerShell is a very recent blog post written by Ashley McGlone:
Practical PowerShell Security: Enable Auditing and Logging with DSC
What about AV and how it can be bypassed?
AV should never be your only layer of protection. Next-gen or not.
What about... ?
Where there are attackers, there are defenders and vice versa. Use Event Logging. Use Sysmon.
I'm a red teamer, where can I find more information?
A recent post by Artem Kondratenk offers a ton of resources and insight:
A Red Teamer's guide to pivoting
Can I use this data?
Of course! As long as you mention the original source, which is this exact blog post. You may find a direct SurveyMonkey link to the results here.
Thanks to all the participants, and to you for reading!
Please do comment with your feedback or questions or anything else you would like to discuss.

No comments:
Post a Comment