When a website is serving up malware to unsuspecting visitors, it's often not too hard to find the culprit. In some cases however, it takes a bit more digging. When visiting a (not named on request) specific website, you're presented with the following message:
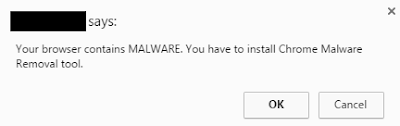 | ||
| Your browser contains MALWARE. You have to install Chrome Malware Removal tool |
After some digging on the site, nothing was suspicious at first sight. However... It did have a EU cookie law pop-up/consent:
The script behind it is as follows:

... Which contains:
Both scripts contain the warning message and a redirect to the Google Chrome store:
lang = 'en';
var msg = 'Your browser contains MALWARE. You have to install Chrome Malware Removal tool.';
if (lang == 'es') msg = "Su navegador contiene malware. Usted tiene que instalar la herramienta de eliminación de malware Chrome.";
if (lang == 'it') msg = "Il tuo browser contiene malware. È necessario installare strumento di rimozione malware Chrome.";
if (lang == 'fr') msg = "Votre navigateur contient MALWARE. Vous devez installer l'outil de suppression de logiciels malveillants Chrome.";
if (lang == 'pt') msg = "Seu navegador contém malware. Você tem que instalar o Ferramenta de remoção Chrome Malware.";
if (lang == 'de') msg = "Ihr Browser enthält MALWARE. Sie müssen Chrome Malware Removal Tool zu installieren.";
if (lang == 'ru') msg = "Ваш браузер содержит вредоносный код. Вы должны установить расширение для блокировки вредоносного кода.";
if (lang == 'gr') msg = "Το πρόγραμμα περιήγησής σας περιέχει κακόβουλο λογισμικό. Θα πρέπει να εγκαταστήσετε το Chrome Malware εργαλείο αφαίρεσης.";
You can find both scripts on Pastebin here and here.
| Chrome Malware Removal Tool |
At time of writing, it has over 22,000 users. You can find the malicious extension here.
UPDATE 27/07: the malicious extension has now been removed from the Chrome store.
To remove an extension from Chrome:
It is not clear whether the site offering the cookie consent script is hacked, or is in on the ploy. The following URLs are leveraged in this campaign:
| Type | Indicator |
|---|---|
| URL | http://cdn.front.to/libs/cookieconsent.min.js |
| URL | http://cdn.front.to/libs/cookieconsent.min1.js |
| URL | http://cdn.front.to/libs/cookieconsent.min2.js |
| URL | http://cdn.front.to/libs/cookieconsent.min3.js |
| URL | http://front.to/libs/cc_test.js |
| URL | http://front.to/libs/cc_test_alert.js |
You can find further indicators as always on AlienVault OTX.
Conclusion
Stay clear from scripts offered by 3rd party EU cookie consent websites and rather create your own pop-up. A trustworthy site to create this for example is cookie-script.
As always when managing a website, keep your CMS (if any) updated as well as any plugins that may be running.
You can find more tips on how to prevent, find (and remove) malicious scripts on your website here.


The original Cookie Consent javascript was created by Silktide. https://silktide.com/tools/cookie-consent/
ReplyDeleteThey seem to host the script on Cloudflare, and it doesn't seem to have this malware.
http://cdnjs.cloudflare.com/ajax/libs/cookieconsent2/1.0.9/cookieconsent.min.js
So in this case it looks like someone has downloaded it, edited to to include the malware and then uploaded it to front.to. I'm not sure if front.to is a legitimate CDN or simply set up to facilitate this.
Hi Garve!
DeleteThanks for your comment - I agree that it seems like that. The 'weird' part is that the front.to CDN is also hosting a legitimate cookie consent here:
http://cdn.front.to/libs/cookieconsent.min.4.js
The ones <4 do however have the bad JavaScript included. Hence it's not very clear if both that site and the CDN are in on it together. (it is suspicious though that they're both hiding behind CloudFlare and have exactly the same design set up).
In any case, I've contacted front.to but no reply yet.
Feel free to add anything you can think of and thanks for your comment.
Regards
Bart
Email bounces from the cookie site, zero response from the CDN - I think we can conclude they are in on it together :)
DeleteVery well explained because i was having some troubles with this fake chrome extensions, thanks for the information
ReplyDeleteI had problems on Firefox displaying a fake virus alert and redirecting to an advertising site. Thanks to your info I found it came from the cookie accept script that I had installed from a third party so I've now installed the one you recommended.
ReplyDelete