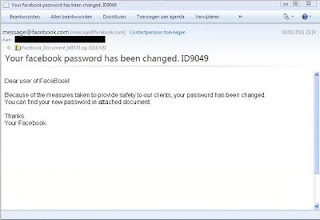
A recent spam campaign is spreading claming your Facebook password has been changed, and you need to open the document attached to view your new password.
You might think: "Why attach a document with the password in ? Why not just put it in the email ?"
The truth is of course is that your Facebook password hasn't been changed at all, it is the latest spam campaign trying to infect your computer.
I received the following email with subject:
Your facebook password has been changed. ID9049
Your Facebook password has been changed
Attached is a ZIP file called Facebook_Document_Id0573.zip. Included is the following file:
Facebook_Document.exe, seemingly a Word document
Does this look like a Word document ? Yes
Is it a Word document ? No
How can you tell ? By the .exe extension
Facebook_Document.exe
Result: 35/43 (81.4%)
MD5: e354e01caea7c9e8171a0e839d5016b6
Anubis Report
Additionally, the file tries to connect to:
hxxp://interviewbuy.ru
Domain Hash: 0d251df39c785768e0b9af27880fcc0f
Result: 6/18 (33 %)
URLVoid
Conclusion
Additionally, the file tries to connect to:
hxxp://interviewbuy.ru
Domain Hash: 0d251df39c785768e0b9af27880fcc0f
Result: 6/18 (33 %)
URLVoid
Conclusion
If you receive emails like this, you should already be alerted:
"Why would Facebook send me an email my password is changed ?"
They don't. Whether you have Facebook or not, instantly delete the email. In this case, the file was zipped but there was no password.
If your email provider doesn't stop it, your Antivirus should. Keep everything up-to-date people !
I would like to add the blogpost Dancho Danchev made, it is the same spam campaign but with another subject and another malicious executable: